The performance of IoT systems depends on the coordinated work of all the devices that form an IoT architecture. In this article, we will focus on IoT architecture, its most important parameters, and the layers that enable flawless deployment and easy implementation in many spheres of human life.
Introduction
Internet of Things architecture is a complicated organization comprising many structural elements working in tandem. Their concerted efforts ensure the coordinated performance of any kind of IoT system, be it for industrial, business or personal use.
Lighting in smart homes can turn on and off automatically, and heat and humidity can adjust to the most optimal levels quickly and smoothly, almost with no human intervention at all. What makes this possible?
Get SaM Solutions’ IoT consulting or development services to deliver a competitive IoT product cost-effectively.
IoT Architectures
IoT architecture is a system of constituent elements, network structure, and cloud technologies that operate in compliance with established IoT protocols and security standards.
Constrained Devices
Constrained devices form the basis of the Internet of Things ecosystem. As the name implies, these devices are compact and have low energy consumption. They include sensors, actuators and controllers that react to the changes in the external world. Their function is restricted to the few major tasks they perform. Relatively inexpensive, they are affordable and are aimed at high-volume manufacturing.
Gateways
Gateways manage the connection between constrained devices and the outer network. The gateway is usually a material object, but other gadgets can sometimes perform its function.
IoT Cloud Platforms
In the Internet of Things, cloud platforms denote the software infrastructures and services that are used in the IoT system. As a rule, they function in a cloud or data center. These platforms can be scaled for use by a larger number of gadgets or in more software solutions. Their most important characteristics are:
- increased interworking in the system;
- better connectivity and ability to collaborate with multiple devices that use various sets of rules;
- provision of necessary updates;
- data management and preservation;
- data consolidation and analysis;
- reporting and visualization.
Why Do You Need a Robust Internet of Things Architecture?
IoT technologies can bring huge benefits for businesses from different domains. A high-quality IoT system is highly functional, scalable and easily maintainable by users. It is easier to manage your devices and sensors with a revolutionary IoT approach, as it enables remote access, improved security, and more convenience overall.
Despite the obvious benefits offered by the technology, some companies are still reluctant to give IoT a try. The most likely reason might be that, because there is significant diversity in Internet of Things solutions, people may be lost and not know where to start.
Let’s consider the most valuable advantages of IoT for business and personal use. Smart devices equipped with sensors improve the quality of life of individuals and provide an enhanced user experience, which leads to more customer satisfaction. With an elaborate Internet of Things architecture, employers can utilize resources more efficiently and minimize expenditures of human labor. For business owners, it becomes easier to manage workflows and make thoughtful and informed business decisions based on precise data received from IoT devices.
When you decide to incorporate IoT into your network, make sure it is installed and maintained by professionals. If your IoT infrastructure is not set up properly and lacks important technical features, it can result in data leakage and extra expenses on maintenance services.
Building Blocks and Layers of IoT Architecture
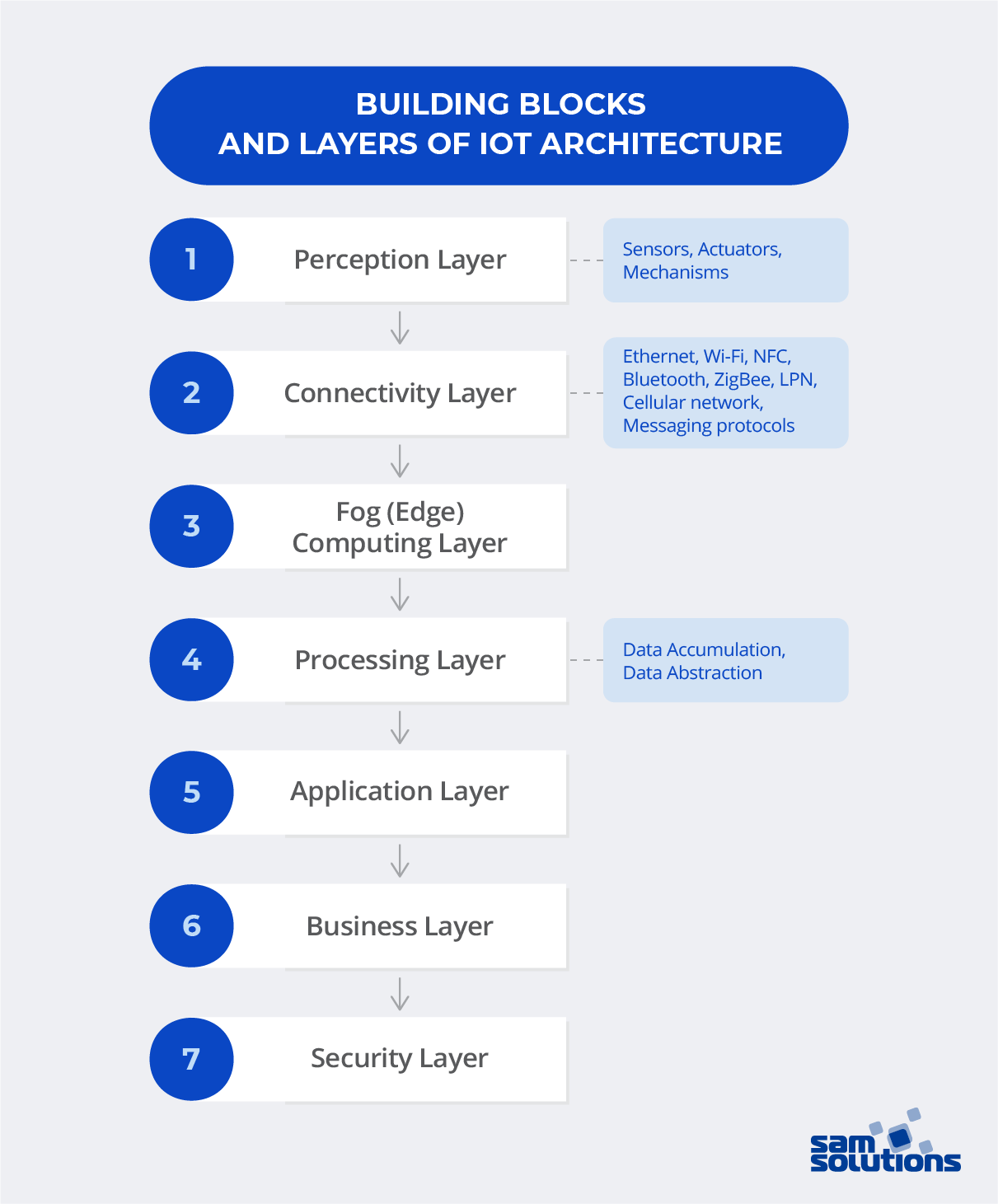
Perception Layer
The first step of core IoT infrastructure functioning comprises a number of special devices equipped with sensors that take on the role of intermediators between analog and digital worlds. These devices have various forms and sizes, and are separated into three distinct categories.
Sensors, as a rule, are small devices that gather the lighting, humidity and temperature values, transform them and then forward the data to IoT systems. They have low energy expenditure and are relatively economical.
Actuators are used to convert electrical signals, which results in actions that are physically performed by devices. An example of their work can be laser robot-assisted surgery.
Mechanisms are all other gadgets that are involved in system functioning.
Mechanisms are connected to sensors and actuators or contain these as integral parts.
Connectivity Layer
The next stage is the connection between all the devices, sensors and services that function together. These can be connected in two different ways:
- Direct connection (TCP, UDP/IP)
- Gateway connection (using modules that can translate, encrypt and decrypt data)
Various network techniques are used to establish communication:
- Represented by a group of connected gadgets within a local area network, the Ethernet connects devices through a physical cable according to a number of rules. It is widely used across different industries, including in home security.
- Wi-Fi technology does not require any wiring to transfer data or carry out other actions. The system uses fast light or radio waves. For instance, smart homes widely use Wi-Fi to connect the lighting system and mobile phones.
- Near Field Communication (NFC) is used for communication of compatible gadgets in close proximity to one another. One of the devices transmits data and the other receives it. Some devices can both send and receive data. A good example of such a device is a smartphone.
- Bluetooth is the technology that uses radio waves to transfer data between neighboring devices. No wiring is needed. However, only small amounts of data can be transferred, so large documents cannot be shared.
- Low-power networks (LPN) provide long-radius connections between devices with sensors that regularly send data at a low bit rate. This technology is often used in infrastructure in smart cities, smart buildings or in agricultural activity.
- ZigBee is a wireless technology created to leverage low-power digital signals. Multiple devices, connected by this method, can interact with each other. It’s mostly used to automate IoT systems in homes, but it can also be used in industry, science and healthcare.
- Cellular network is a system with high speed and large capacity, which enables contact between cellular devices. It is used for telephone calls, data sharing, business collaboration and intercommunication in cases of emergency.
- For safe data sharing, IoT infrastructure uses messaging protocols. These are the rules for messages transmitted between devices equipped with smart sensors. These rules stipulate that messages include a certain type of information in a set format.
Fog Computing Layer
Fog (Edge) computing layer is aimed at quick data storage near its sources. This layer makes it possible to analyze and transform large amounts of data in real time near its original sources. It is a time- and resource-saving approach that results in quicker system response and overall improved functioning. The 5G mobile communications standard uses this method to ensure stability and smooth secure operation along with high speed.
This layer can operate on the gateway, server, etc. It evaluates the data and identifies if there is any need for extra computation, formats, decodes, or filters. It then redirects the data.
Processing Layer
While the previous layers are used for constant data modification, this is not the case at the processing layer. This layer is responsible for accumulating, storing and processing information received from the fog computing layer. Actions performed at this layer are divided into the following steps:
Data Accumulation
APIs receive information in real time, and store it according to rules and specifications to make the data available to the non-real-time system, such as that of a desktop computer, workstation, or accounting system. This stage is the junction between the generation of data based on events and the consumption of data based on queries.
Moreover, this stage specifies if the information corresponds with the company’s needs and determines where to place it. The ultimate objective is to arrange unstructured data and ensure its efficient storage.
Data Abstraction
This stage finalizes the data for subsequent use by client apps. As a rule, this process includes the following steps:
- Consolidation of data received from various resources
- Reconciliation of different data formats
- Virtualization or aggregation of data so that it can be accessed remotely
App-layer information undergoes reformatting, and is then sent to the physical level in a way that is comprehensible for gadgets.
These steps of the processing layer enhance the interaction between the components of IoT systems and free engineers from having to personally deal with it.
Application Layer
At this point, data undergoes analysis by software programs and apps with the aim to provide the answers needed to make well-thought-out business decisions. Currently a great number of apps exist that differ in their functions, implemented operation systems and technologies. Among them, you can find software that monitors and controls the devices, uses ML techniques, BI and analytics tools.
Business Layer
When making decisions regarding any business change, it’s useful to take into account data gathered previously. The business layer helps companies adjust their business strategies and make more thoughtful plans based on the right data. It enables them to dive deeper into the issues that need to be resolved, as well as their causes, and predict possible consequences.
Security Layer
Big companies/suppliers of IoT devices install high-level security by default, but the ability to add additional protection features once the system is in use is of paramount importance. There are four major levels of device security:
- Device-level: producers of IoT gadgets try to add special protection in the hardware and firmware by default. Some examples are TPM microcontrollers that preserve artifacts responsible for platform authentication; safe booting that does not allow intervention without valid authentication credentials; frequent updates; hardware safeguards.
- Connection-level: Confidential data should undergo encryption. To achieve this, IoT application messaging protocols are used.
- Cloud-level: Data in the cloud should undergo encryption for the sake of risk mitigation. This helps protect confidential information against cybercriminals. Special authentication and authorization technologies prevent unapproved third parties from using IoT applications. Devices are also checked for credibility before connecting to the cloud storage.
Stages of IoT Architecture
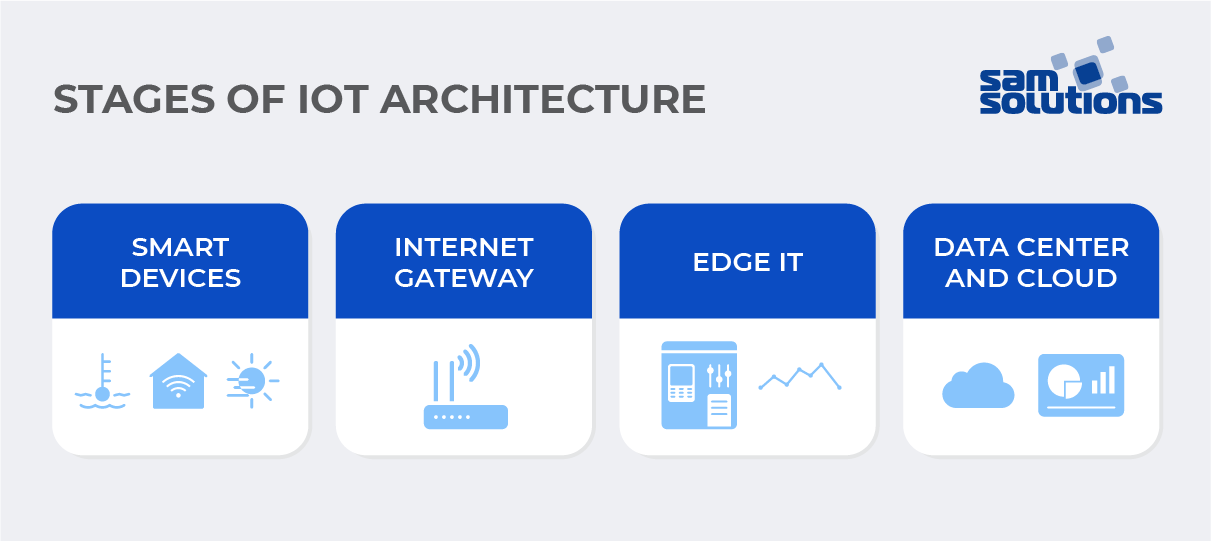
The IoT system should be capable of providing stable support to IoT architecture. The following stages are meant to make IoT usage efficient and viable to your business.
Smart Devices
The first stage of IoT architecture includes devices such as sensors, actuators and controllers that aggregate sensor data from the environment or interconnected objects and transform it into data that can then be used by clients. Sensors are responsible for detecting fluctuations in lighting, temperature regime, motion, pressure, etc. The controller then receives the signal from the sensor, reworks it and transmits to the actuator. The actuator can then lower or increase the temperature, light, or humidity level.
Internet Gateway
Internet gateways are usually located in the immediate vicinity of sensors, actuators, and controllers. After they receive the data, it is aggregated and converted from analog to digital form with the help of data acquisition systems. The converted data subsequently goes into the Internet gateway, which forwards it to the next stage.
Data preprocessing into digital form is pivotal for quick system functioning, as analog datasets are heavyweight and occupy a lot of space. Moreover, the structure of analog data is inconvenient to deal with. That’s why this change is essential.
Internet gateways can add extra functions to be capable of managing data, real-time security, and analytical activities. As a rule, the devices at this stage are compact and movable, and made from protective materials so that they can survive harsh weather conditions.
Edge IT
Edge devices are most frequently placed on-site or near a particular data source, but can sometimes be located in remote locations as well. Data in digital form undergoes edge IT computing, with more analysis and processing in particular.
This is done before the data is sent to cloud storage or data centers. Edge IT computing alleviates the burden otherwise laid directly on the data center. It reworks the raw data into a more convenient form and then sends it further. This stage also helps ensure more safety for your confidential information and speeds up data processing. For example, it can convert huge amounts of data and visualize it into a comprehensible graph, map, or dashboard that is easy to understand and doesn’t take up much space.
The Data Center and Cloud
At the last stage, the data is sent to physical data centers and the cloud to undergo a thorough analysis, management, and storage in compliance with security best practices. This procedure can occur in the physical office, on the cloud or in the combined system (for example, the one that is in-house but with cloud-based services).
Open Source Solutions
The world has witnessed the domination of open source technologies in operating systems and big data software like Apache Hadoop. There are open source technologies that can also help IoT infrastructure deal with constrained devices, IoT gateways and cloud stacks.
Using IoT Architecture in Your Business Software
With IoT architecture, businesses streamline workflows, enhance productivity and consequently boost return-on-investment. Structured information and thorough big data analysis help drive more efficient performance at all levels, leaving no room for wrong business decisions.
Customized programs in combination with IoT solutions allow users to have more power over all the activities that occur in the system. Thanks to automated processes in IoT architecture, it is easier to monitor and control the processes, even in remote mode. Business owners receive notifications if something in the system gets out of order and can take the necessary actions to resolve the issue immediately.
Example of Internet of Things Architecture
Let’s take a look at Internet of Things architecture using the example of an IoT-based smart home system. This can comprise a multitude of connected devices equipped with smart sensors: coffee machines, TV sets, security, lighting and electricity systems, and even smart plant pots. All these gadgets can be connected to one another and can be easily monitored and controlled by the homeowner via an app.
In smart homes, sensors can detect and measure physical characteristics of the environment such as humidity, heat, and lighting. If these measurements are not in conformity with the required values, the system sends notifications to the users via Wi-Fi Internet. The values can be adjusted either automatically as set by the user, or manually by remote control via smartphone or laptop.
With SaM Solutions’ wide range of IoT services, you get professional support and hands-on assistance at any stage of your IoT project.
Conclusion
Thanks to the emergence of Internet of Things, many spheres of life have undergone significant changes. Our workplaces, businesses and even homes are connected to the Internet. All these IoT infrastructures may be different in purpose, but have one thing in common — their major elements and layers. A good IoT infrastructure should accommodate business requirements and be functional, scalable, available, maintainable, and cost-effective.
For a highly efficient and secure IoT system, professional expertise is vitally important. At SaM Solutions, we offer a versatile approach to deliver customized software that will suit your business needs perfectly and help you smoothly enter the IoT community. Don’t hesitate to contact us for more detailed advice for your enterprise.



























 5 Reasons Why Your Business Needs a Mobile eCommerce Application
5 Reasons Why Your Business Needs a Mobile eCommerce Application Using Salesforce to Improve Your Sales Pipeline: Five Tips
Using Salesforce to Improve Your Sales Pipeline: Five Tips Cross-Platform Mobile Development: Five Best Frameworks
Cross-Platform Mobile Development: Five Best Frameworks How to Develop Custom Accounting Software
How to Develop Custom Accounting Software 10 Best Web Development Frameworks in 2024
10 Best Web Development Frameworks in 2024











 Top 30 Ecommerce Tools to Elevate Your Business in 2024
Top 30 Ecommerce Tools to Elevate Your Business in 2024 5 Best Tools to Improve Embedded Software Testing
5 Best Tools to Improve Embedded Software Testing Why React and Node.js Are the Top Technologies for Creating High-Performance Web Apps in 2024
Why React and Node.js Are the Top Technologies for Creating High-Performance Web Apps in 2024 10 Best IoT Platforms for 2024
10 Best IoT Platforms for 2024
I use smart home IoT on a daily basis. The system regulates the temperature and humidity in my house, and automatically activates my devices when I need them. I really like IoT and can’t wait till it’s more widespread in my area.
I find the idea of IoT infrastructure a bit difficult to grasp. Nevertheless, I can’t deny that a properly set infrastructure could bring numerous advantages both for private and industrial use.
I am thinking about trying Internet-of-Things technology for my business. I studied your article and think that it could improve the quality of my products and enhance the customer experience.
The most marvelous realization that came to my mind is that the IoT infrastructure is similar to our body in functioning when each component is in close connection to the others and can influence the work of the entire system.
I think businesses should pay more attention to the perception layer. I recently had some problems with my sensors and actuators, which were displaying data incorrectly.
I think IoT security is pivotal for any Internet-of-Things infrastructure. Glad to know that my devices are equally protected at device, connection and cloud levels.
Thank you for the article. I now have some insight into which spheres of IoT infrastructure I can use to upgrade my department for better performance.